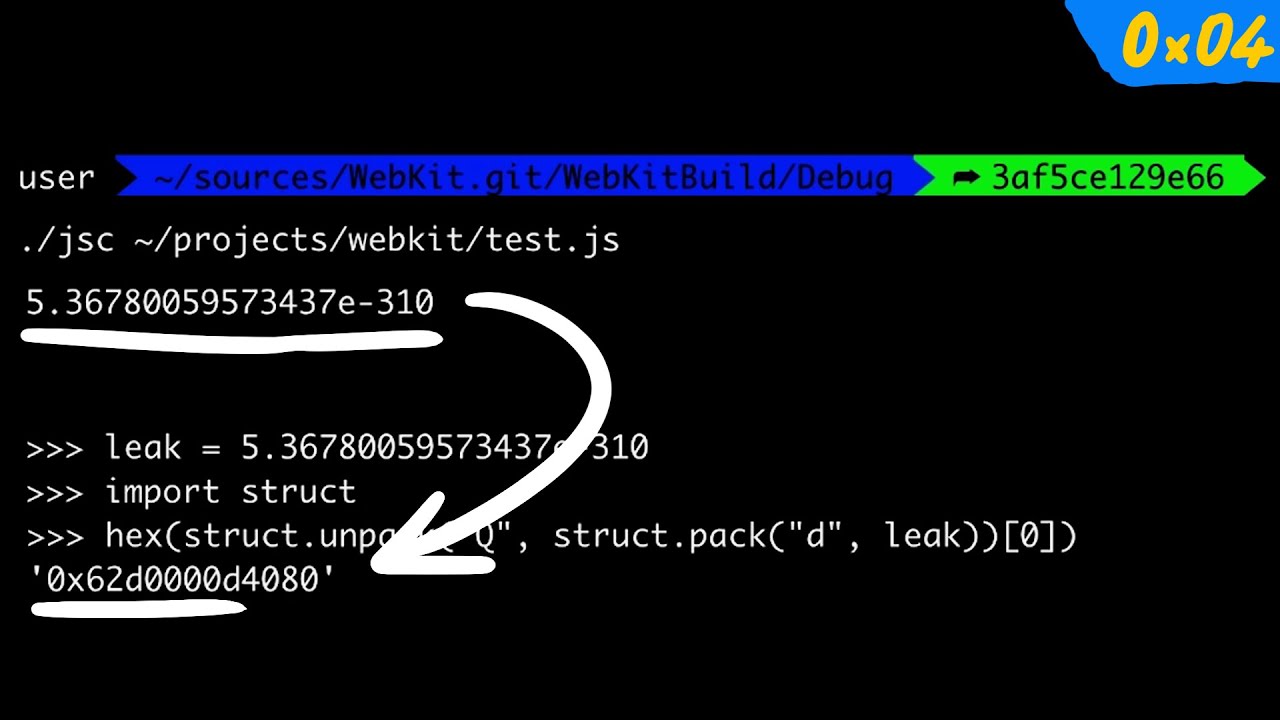
Prototype pollution: The dangerous and underrated vulnerability impacting JavaScript applications | The Daily Swig
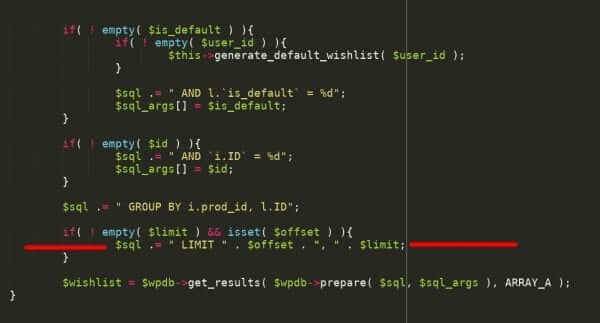
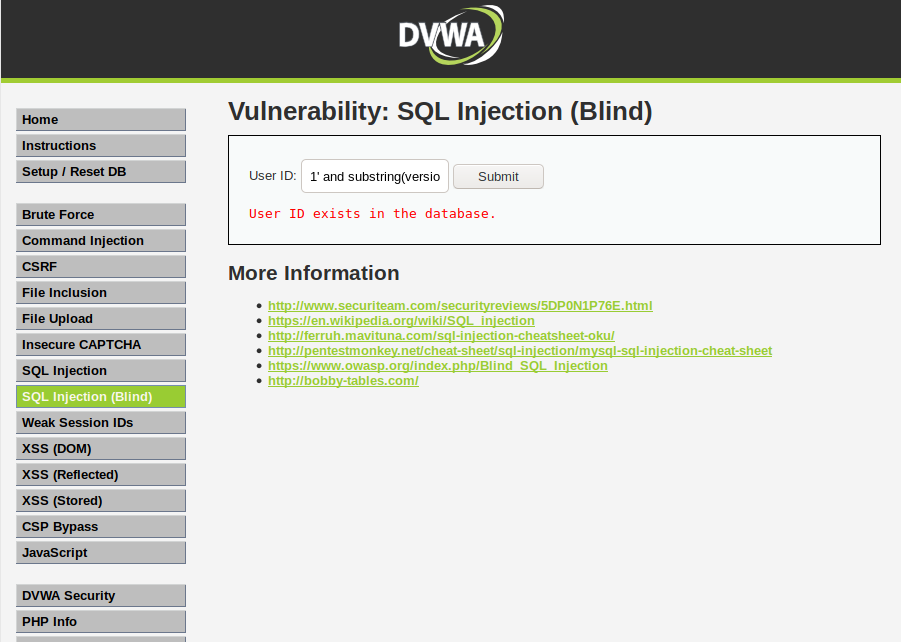
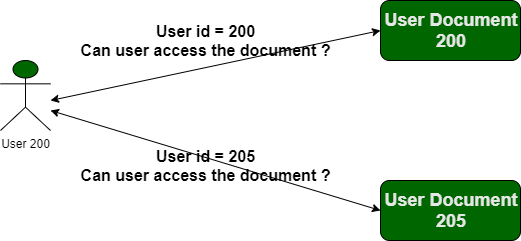
10 API Security Vulnerabilities You Need To Be Aware Of (Along with REST API Overview) | by Santosh Shinde | JavaScript in Plain English

Sumita Chakraborty on Twitter: "“I guess the reason I don't like to hear / His stories ... / Is because I'm afraid to know he was ever so vulnerable”: I love this

Caleb on Twitter: "Jake Paul vs Tommy Fury rigged?! I guess Tommy going home with nothing after that bet. John ffs, that mf had to open his mouth. https://t.co/IW8JQ9QNBx" / Twitter

Remote code execution vulnerability exposed in popular JavaScript serialization package | The Daily Swig